Table of Contents
( http://puck.nether.net/pipermail/cisco-nsp/2004-November/014090.html )
Normally, through a switch port, there are 3 kinds of traffic that are forwarded (i didn't take into account the vlan separation in the switch):
- ethernet broadcast packets (dest mac ff:ff:ff:ff:ff:ff)
- traffic for the mac addresses learned on the port
- traffic with dest. mac addresses unknown to the switch, which is flooded to all ports but the one where the packets entered.
When one uses “switchport block unicast”, the third type on the list, the so called “unknown unicast” traffic is not forwarded to the specific port, so the only traffic exiting the port will be the broadcast (ff…) or the packets that have as destination mac, one of the mac-addresses learned on the port.
A problem arises when a host connected somehow to that port does not send any traffic for more than $mac_address_aging_time (usually 5 min): the mac will be erased from the mac address table, and the traffic will
not be forwarded to the port (due to the blocking of unknown unicast) until a packet is received again and the mac is relearned. This setting should be mostly used on port with hosts connected, not a “core” port. On most of the cases, there will no problems, since all operating systems (programs, daemons, servers) send packets, and one of these
packets is enough to make the mac address of the host be addded to the table on the switch, and the probability of a “normal” host to not send packets for 5 minutes (especially if it is Windows :) ) is very very small.
PoE (Cisco that's not using 802.3af by default)
interface fa x/y power inline delay shutdown 5 initial 100
for each interface
Make Catalyst switch silent (The Invisible Catalyst Switch)
Original notes: http://packetlife.net/blog/2010/apr/15/invisible-catalyst-switch/ (10x Jeremy Stretch)
Turning off CDP
S1(config)# no cdp run
Turning off DTP
S1(config)# interface range f0/1 -24 S1(config-if-range)# switchport mode access S1(config-if-range)# switchport nonegotiate
Turning off STP
S1(config)# no spanning-tree vlan 1
Turning off Ethernet Keepalives
S1(config)# interface range f0/1 -24 S1(config-if-range)# no keepalive
Security on L2 based equipment
see Security Features on Switches on Access Lists
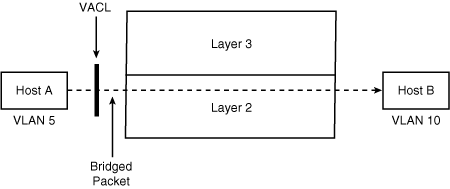
VLAN ACL (VACL)
Configuring VACL
- Define the standard or extended access list to be used in VACL.
- Define a VLAN access map.
- Configure a match clause in a VLAN access map sequence.
- Configure an action clause in a VLAN access map sequence.
- Apply the VLAN access map to the specified VLANs.
- Display VLAN access map information.
Switch(config)#access-list 1 permit 192.168.1.0 0.0.0.255
Switch(config)#access-list 2 permit any
Switch(config)#vlan access-map mymap 10
Switch(config-access-map)#match ip address 1
Switch(config-access-map)#action drop
Switch(config-access-map)#exit
Switch(config)#vlan access-map mymap 20
Switch(config-access-map)#match ip address 2
Switch(config-access-map)#action forward
Switch(config-access-map)#exit
Switch(config)# vlan filter mymap vlan-list 5-10
Switch(config-access-map)#end
Switch# show vlan access-map
Vlan access-map "mymap" 10
Match clauses:
ip address: 1
Action:
drop
Vlan access-map "mymap" 20
Match clauses:
ip address: 2
Action:
Forward
Switch# show vlan filter
VLAN Map mymap is filtering VLANs:
5-10
MAC ACL
MAC ACL, also known as Ethernet ACL, can filter non-IP traffic on a VLAN and on a physical Layer 2 interface by using MAC addresses in a named MAC extended ACL. The steps to configure a MAC ACL are similar to those of extended named ACLs. MAC ACL supports only inbound traffic filtering.
Switch(config)# mac access-list extended my-mac-acl Switch(config-ext-macl)# deny any any aarp Switch(config-ext-macl)# permit any any Switch(config-ext-macl)# exit Switch(config)# interface Fastethernet0/10 Switch(config-if)# mac access-group my-mac-acl in Switch(config-if)# end Switch#